Link prediction
Networks are crucial in modeling interactions observed in experiments or data processing. However, it’s essential to consider that many interactions might be overlooked and some observed ones might be artificial: which means that the observed network is a “noisy” observation of the actual network .
Reconstruct given has multiple applications:
- Finding missing links, which can suggest ad-hoc experiments.
- Deleting spurious links.
- Predicting future links in time-varying networks, such as forecasting future friendships.
Different way to do quantifying structural similarity of nodes, examples:
- Common Neighbours: check for each pair of nodes the number of common neighbours and then sort them based on this “score”. In an undirected, unweighted network with adjacency matrix , the number of common neighbours of nodes and is .
- Katz index: a generalization of common neighbours
- Preferential Attachment Index to sort the nodes . The nodes with highest should be connected.
- Resource allocation which doesn’t consider just the common neighbours but also how many links has this neighbour. The rationale here is that a neighbour with a lot of links doesn’t allocate too much resources to and ” so it’s not relevant in the similarity score.
Recommender Systems
A similar formulation of the link prediction problem is to consider a set of users and a set of objects .
The Bipartite Network Representation represent the user-object relationships where:
We can then define:
- User Degree as Number of objects owned by user
- Object Degree as the number of users owning object .
Assuming users like the objects they own, predict and recommend additional objects they might like.
- Global Ranking Method: Recommend objects with the largest degree , implying the most commonly owned objects. This approach lacks personalization.
- Content-Based Filtering: Define object similarity and recommend to user objects most similar to those they already own. This method offers personal recommendations without utilizing network structure.
In collaborative filtering, the main assumption is that similar users like similar objects.
The score assigned to the (non-existing) pair and . So basically we are looking to the strength on the projected graph where and will be users. We are looking at the strength of the relationship between user and user weighted by a factor .
After found (the “score of recommendation” of object to user ) we can also quantify the similarity between users:
- topological similarity: number of objects in common
- cosine-similarity: each user has a score to object he owns and then just measure the difference between vectors:
Robustness
The robustness or resiliency of a network refers to the network’s ability to maintain acceptable levels of service despite network faults. Network faults are generally modelled as either:
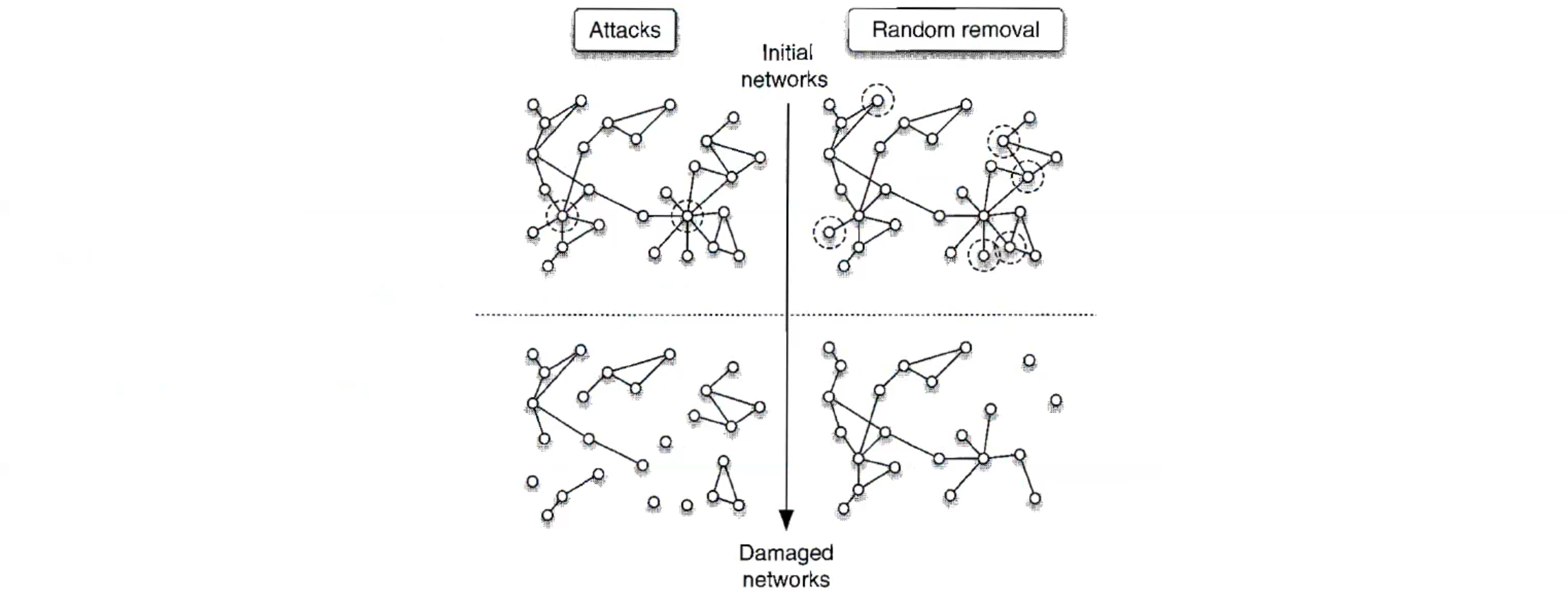
- Failures: Random removal of nodes/links.
- Attacks: Targeted removal of crucial nodes/links (most central or most loaded).
We can measure the impact of removing a fraction of nodes or links by looking the loss of efficiency after removal of all links incident to node :
Different network structures, like the Barabasi-Albert and Erdös-Rényi models, have different responses when nodes or links are removed.
- Erdös-Rényi Networks Under Stress: Homogeneous networks are robust.
- Scale-Free Networks Under Stress: while removing random nodes doesn’t significantly impact connectivity, targeting high-degree nodes rapidly decays connectivity. So they are pretty fragile to attacks.
Motter and Lai model of network breakdown
Understanding the propagation of breakdown phenomena can be interesting.
- Nodes exchange units of material along the shortest path.
- At , node load is proportional to betweenness .
- Node capacity , with as the tolerance parameter.
The key part is that:
- Failure/attack leads to changes in betweenness and thus their load
- The subsequent change of loads can create other node fails since
- These other node failures change the betweennesses : the cycle repeats
At the end is used as a metric with as the size of the largest connected component of the network after a failure or attack has occurred.